Hackers tricking UAE companies to make payments to foreign bank accounts – A real-world case study
تجريب
January 7, 2016
Daily Mail UK Features Torrid Networks on an International Credit Card Fraud
January 12, 2016This case study is in continuation to the press release published at: http://www.torridnetworks.com/press-events/press-releases/uae-companies-being-targeted-by-the-hackers
The entire incident was started with an email sent from a spoofed email address fundtransferdpt@hsbc.com to the victim working in the accounts department of the company. Email contents were convincing enough for any accounts person to open the attachment. Victim was on Google Apps for the corporate emails which didn’t block the malware hidden within the attached file with .ace extension, a compressed file format like winzip. Malware filename was kept as Wire Advise_HSBC0000079652pdf.exe with a PDF icon for the file. With the default Windows settings of hiding the known extensions, the file looks like a perfect PDF document to normal user.
Before proceeding to static analysis or reverse engineering, we thought to perform a quick dynamic analysis of the malware. Although it was partially undetectable by the antivirus systems, the malware was found to be a very basic in nature without any sophisticated mechanisms involved.
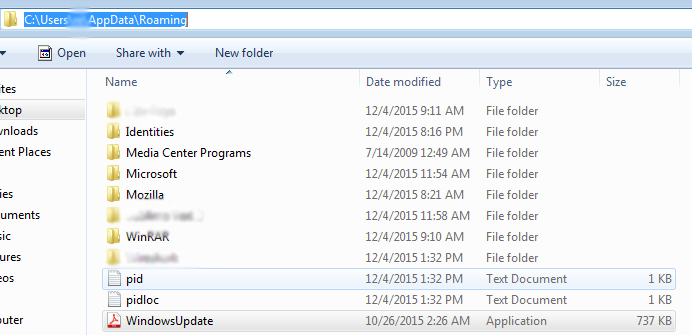
On execution, malware would install itself into the system Roaming folder as can be seen from the screenshot below.
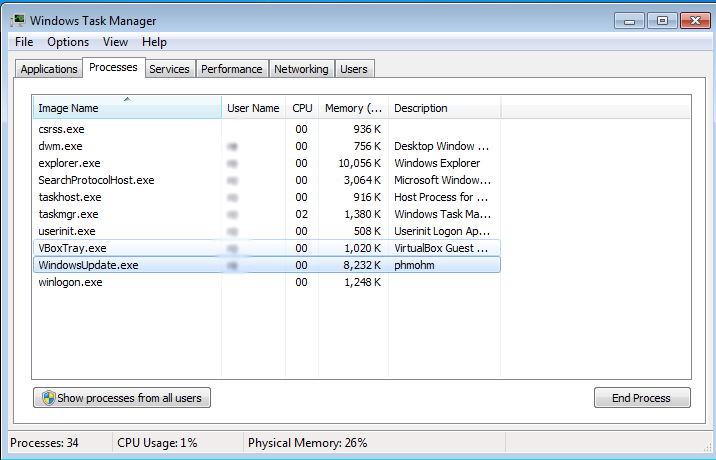
Without using any process injection or rootkit techniques to hide itself, malware can easily be seen in the task manager although the process name might trick a normal user to believe it to be a legitimate process.
Once the malware executes, it starts recording the keylogs, screenshots, browser cache and uploads the recorded data to its operator via email every 40mins.
Destination email address along with the SMTP relay address and the credentials were hard coded in the malware. Also, the destination SMTP port utilized for the data upload was 587 rather than standard port number 25, may be to bypass the firewall rules. The mail server is hosted with GoDaddy and appears to be owned by the hacker, as the SMTP relay used to upload the data is the same as MX for the destination email address.
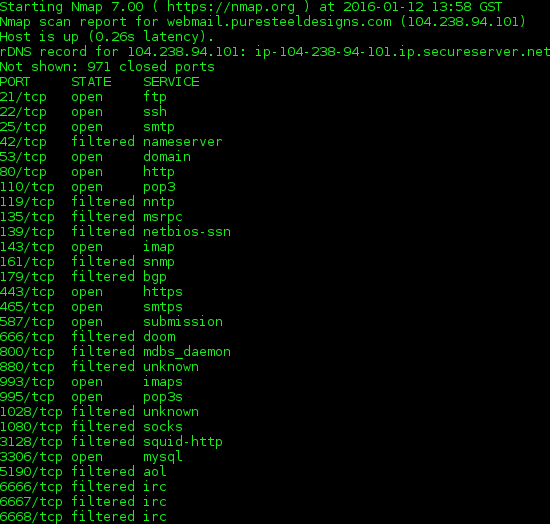
Few of below screenshots could provide more information on attacker infrastructure, definitely doesn’t look like a professional hacker’s infrastructure.
Appears that the attacker has been into business from a while, as can be seen from this VirusTotal link and screenshot below:
Interesting part is that GoDaddy has not been able to track suspicious email traffic in its network and take down botnet CnC from its network.
Malware generates following traffic when executed on the system.
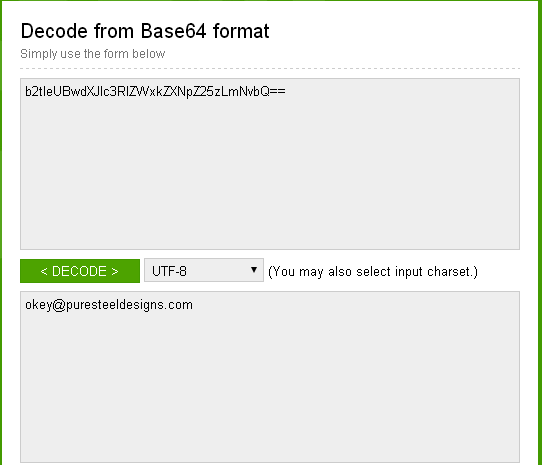
Such mechanism is not expected from a serious and sophisticated malware. In the traffic, SMTP username and password can be seen as base64 encoded strings which can easily be deciphered as can be seen below:
Similarly, password was also extracted. Due to the nature of the task, password is masked in the traffic for discouraging any misuse of the information.
Attacker doesn’t sound to be pro as is visible from the nice looking webmail interface which he is using to monitor his bots.
And its even more evident from the control panel he might be using to manage the server:

His mailbox has a lot of emails and a lot of victims:
Sample email with keylogs with some UAE business details. We have masked the details as a respect to the privacy of the victim.
A sample screenshot on a transaction can be seen from below screenshot:
Apart from this there have been numerous emails with victim’s netbanking details, credentials for social media, email and other portals.
On a concluding note, from the analysis, it appears that the attacker is more of a scammer from Nigeria (as per the domain registration records) and not a professional hacker who might be excellent in social engineering users but definitely not much into hacking.
Torrid Networks helped its client by investigating the entire case and provided them with complete report including root cause of the issue and implemented strong security controls to avoid such cyber attacks in the near future. We hope this case study should be helpful to other in knowing the unknown.
Readers may like to drop us comments/feedback at info@torridnetworks.com